During my regular working schedule, I came across a requirement of providing a claim based authentication in SharePoint 2010.
Following are the steps I followed to achieve it:
1. Create Database
Open Visual Studio/Management Studio and create a database with appropriate name. Note SQL Server Name.
Explore to C:\Windows\Microsoft.NET\Framework64\v2.0.50727 open aspnet_regsql.exe
Click on Next
Select Configure SQL Server for application services option and click Next button. Please see the image below:
Enter SQL Server name that was noted before and Select Database that you previously created.
Now Open your database and check tables in database
You
will find many table in your table that are automatically created.
2. Configure
Membership and Role Provider
a.
By default, you will see a
<connectionStrings/> node within <configuration> node. Specify the
connection string to the database which has been created in the previous
section
<configuration>
Get Assembly Details
<configuration>
Open Run type assembly in it and
click ok:
That would open assemblies’ window.
Select System.Web right click open properties and note
highlighted details b.
Add the membership provider and role provider
within <system.web> tag. See below code for more information.
<system.web>
<membership defaultProvider="FBAMembershipProvider"><providers>
<add connectionStringName="constr" enablePasswordRetrieval="false"
</providers>
</membership>
<roleManager enabled="true" defaultProvider="FBARoleProvider">
<providers>
<add
connectionStringName="constr" applicationName="/" name="FBARoleProvider"
</providers>
</roleManager>
</system.web>
Where type attribute values are from the assemblies that we noted in previous step.Save web.config file and launch the ASP.Net Configuration Wizard by clicking on Website ? ASP.Net Configuration(Project Menu> ASP.Net Configuration). Please see the image below:
Select role and memberships names that you specified in web.config.Click on security tab> click on Select authentication type
Enter
required details of user
3. Create Web Application to implement Claim base authentication
Follow the below steps to create web application and
site collection.
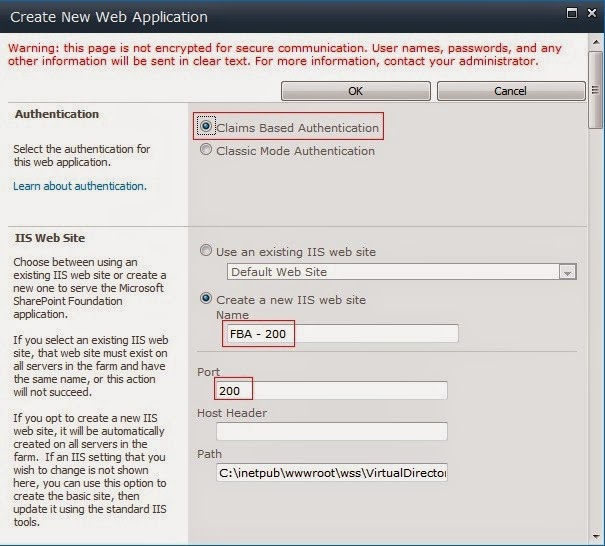
a. Go to Central Administration ? Application Management ? Select ‘Manage Web Application’ link present under ‘Web Applications’ section.b. Click on ‘New’ option in the ribbon. 1. See the below image for ‘Authentication’ and ‘IIS Web Site’ section.
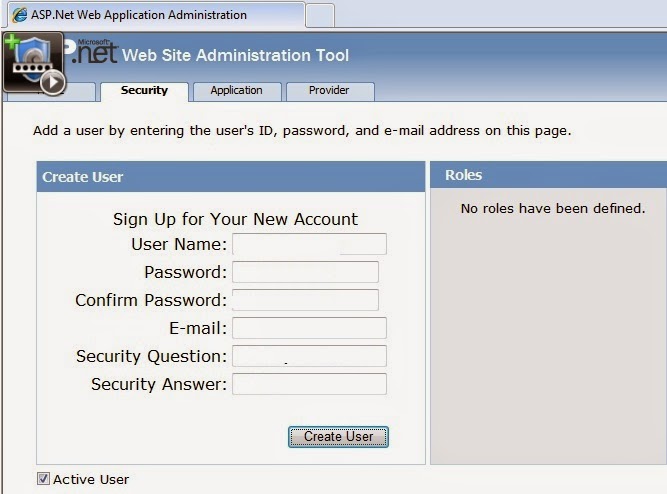
Enter required details of user
1. Create Web Application to implement Claim base authentication
a. Go to Central Administration ? Application Management ? Select ‘Manage Web Application’ link present under ‘Web Applications’ section.b. Click on ‘New’ option in the ribbon. 1. See the below image for ‘Authentication’ and ‘IIS Web Site’ section.

Enter required details of user
1. Create Web Application to implement Claim base authentication
a. Go to Central Administration ? Application Management ? Select ‘Manage Web Application’ link present under ‘Web Applications’ section.
b. Click on ‘New’ option in the ribbon.
1. See the below image for ‘Authentication’ and ‘IIS Web Site’ section.
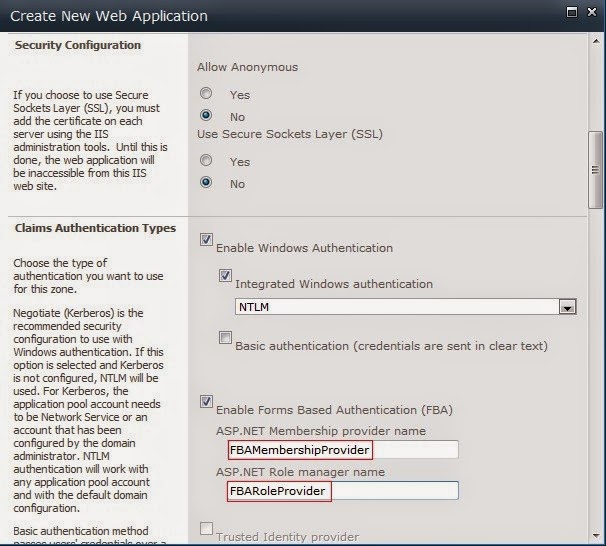
2. See the below image for ‘Security Configuration’ and ‘Claims Authentication Type’ section.
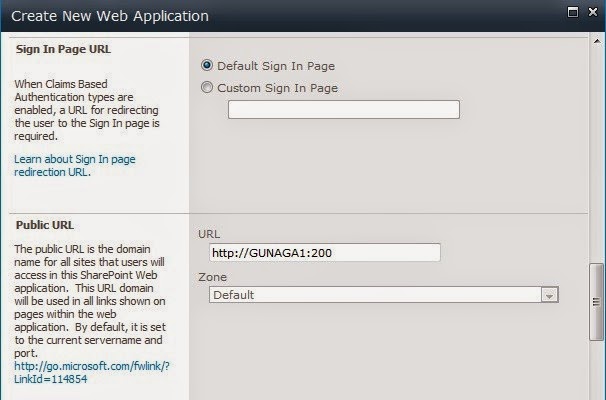
3. See the below image for configuring ‘Sign In Page URL’ and ‘Public URL’ section.
4. See the below image for configuring ‘Application Pool’ and ‘Database Name and Authentication’ section.
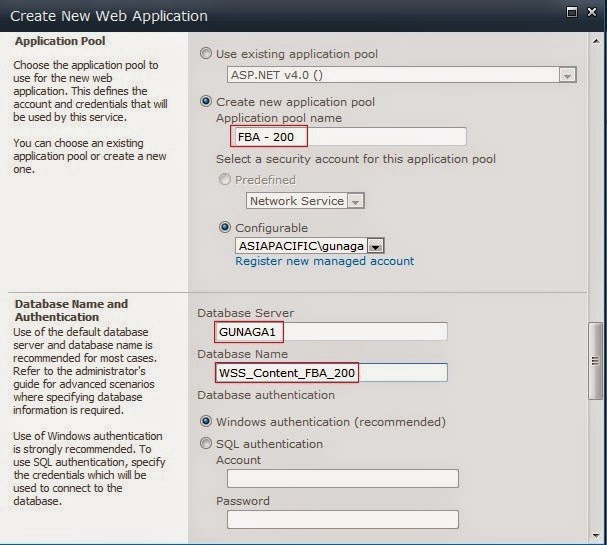
5. Create Site Collection after creating web application. Select the template whichever you want to create site collection.
Note : Do not edit defaultMembershipProvider and defaultRoleProvider property of <Membership> and <Role> tags respectively in any of the web.config file if it is already stated. Also we don't need to add defaultMembershipProvider and defaultRoleProvider properties in SecurityToken web.config file.
4. Now Configure Web.config files of sharepoint sites to use Form based authentication.
- Open IIS Explore > Explore Server name > explore Sites > Select
Central Administration v4 > Click on Explore
> Open Web.config file.
- Copy
<connectionstrings> tag from asp.net web application > web.config that
we created few steps ago.
- Paste
<connectionstrings> tag after </sharepoint> and before <system.web>
in web.config file of sharepoint central administration.
- Add
role to <role manager > tag in central administration web.config. You may
simply copy and paste <add> tag from asp.net web application >
web.config > <role mamager >
that we created.
- Add
member to <membership > tag in central administration web.config. You may
simply copy and paste <add> tag from asp.net web application >
web.config > <membership> that
we created.
- Save
central administration web.config and close.
- Open
IIs and select the web application that we created > Explore > web.config.
- Add
Connection string as we added to Central Administration web.config file
- Add
role to <role manager> and member <membership> tags in web
application web.config file. (Same as we did in central administration
web.config).
5. Configure Security token service web.config file:
Explore to C:\Program Files\Common Files\Microsoft Shared\Web Server
Extensions\14\WebServices\SecurityToken
Open web.config file.
Add
Connection string to <connectionstrings> tag. Role to <role manager> tag
and member to <membership> tag(If you donnt find <connectionstrigs> tag and <system.web> tag in wb.config you need to add it by your self))
6.Add User Policy to our web application
Follow the below steps to add user policy to the web application.
a. Go to Central Administration ? Manage Web Applications ? Select the FBA web application and click on ‘User Policy’ option in the ribbon.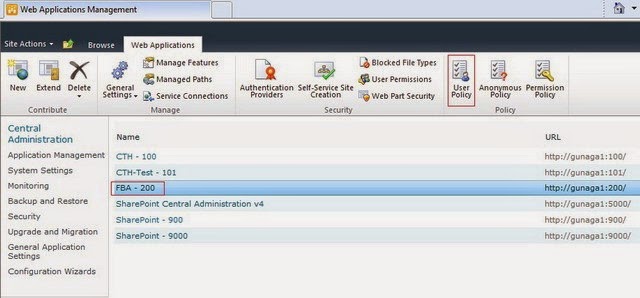
b. Click on ‘Add Users’ link and select ‘Default’ as the zone and click on ‘Next’ button.
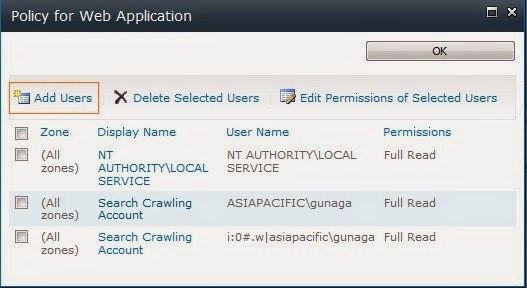
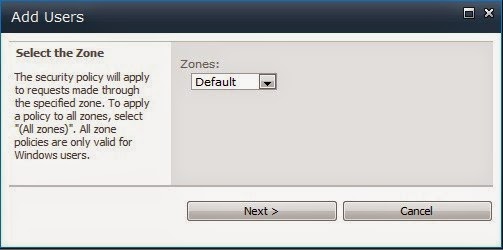
c. Type the user name created in ‘Create User’ section in the ‘Users’ textbox and click on people picker icon. You should see the user name get underlined in the ‘Users’ textbox.
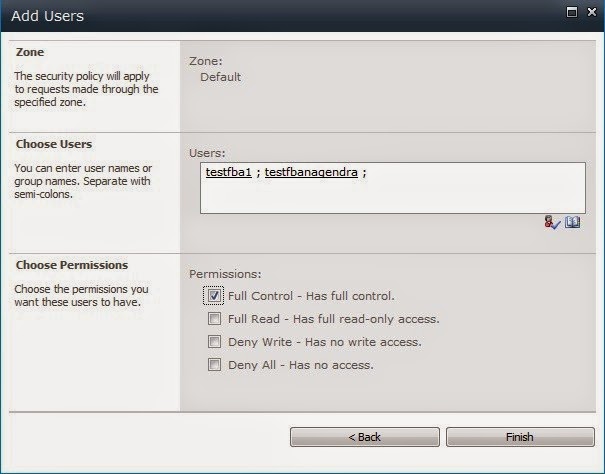
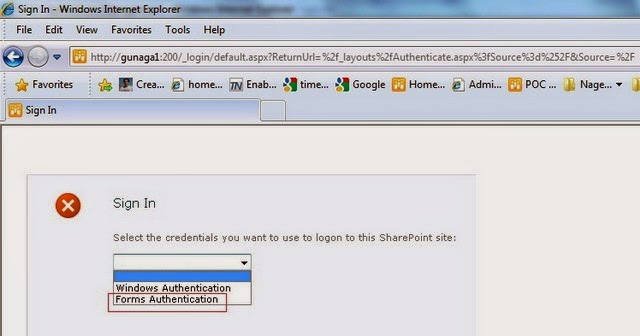
6. Follow the verification steps to test form based authentication.
1. Go to FBA SharePoint site and select ‘Forms Authentication’ option.
2. Enter User Name and Password and select ‘Sign In’ button
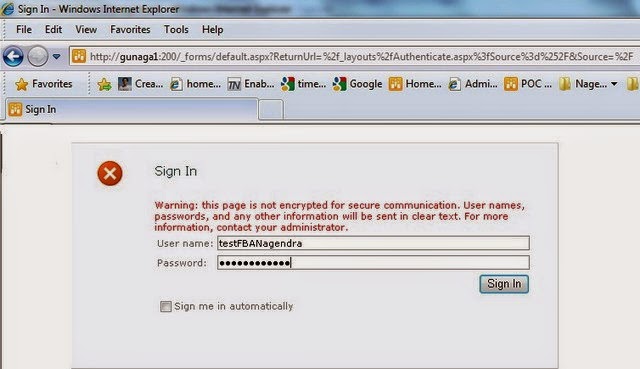
3. You should be redirected to home page.
Regards,
Keyur Pandya
Keyur Pandya













Comments
Post a Comment